Levantamento em 1h
Escolha uma das nossas lojas e faça o levantamento da sua encomenda de forma rápida e gratuitaReceberá uma SMS quando a encomenda se encontrar pronta para levantamento.
Se a encomenda for realizada e faltar menos de 1h para o fecho da loja selecionada a encomenda só estará pronta para levantamento no dia seguinte.
Para usufruir deste serviço, todos os produtos da encomenda devem estar disponiveis na loja selecionada.
Estamos aqui para te ajudar!
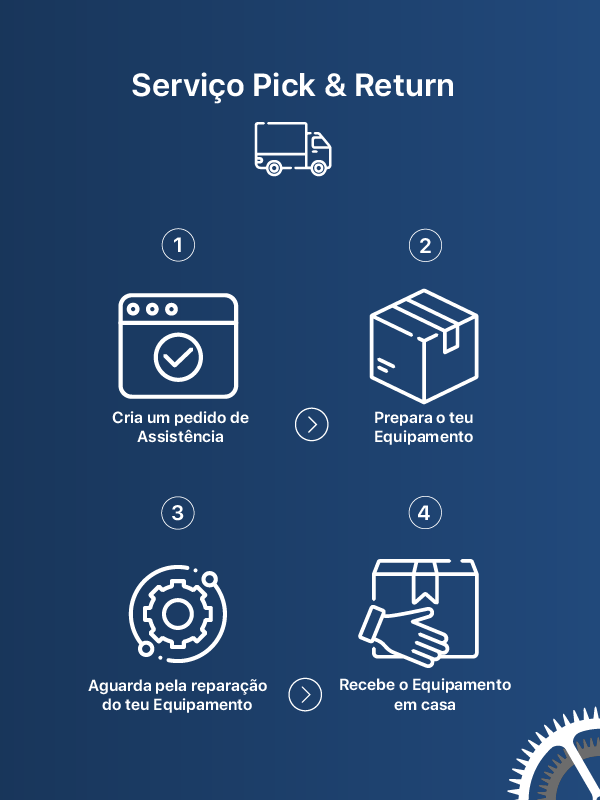
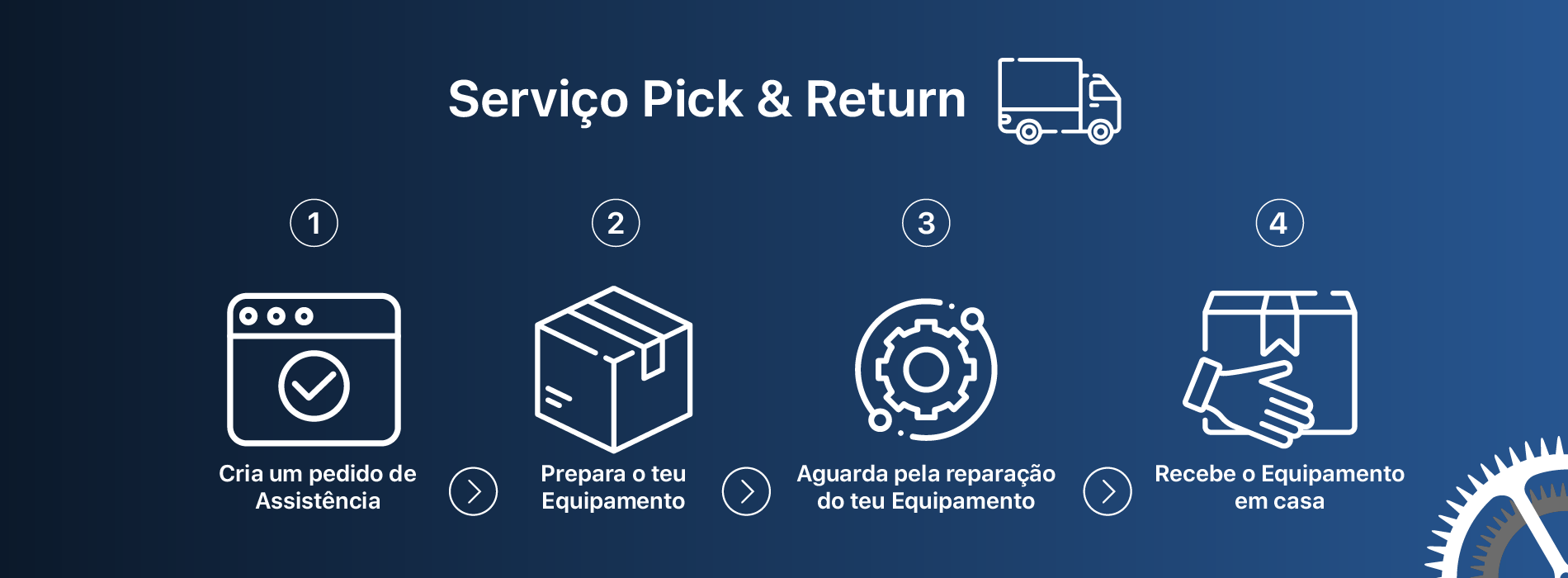
Queres agendar uma reparação em loja ou utilizar o nosso serviço Pick and Return?
Consulta o estado do teu Pedido de Reparação.
O código de reparação está presente no topo da guia de intervenção técnica, logo após o website “www.istoreservice.pt”. Este código é fornecido ao cliente assim que o mesmo dê autorização para reparação de equipamento.
Perguntas Frequentes
Na iStore usamos apenas peças Apple genuínas e componentes originais.
Algumas peças não originais, como carregadores e baterias, poderão ter falhas de conceção que
levem a problemas de segurança.
Existem ainda ecrãs não originais de qualidade bastante inferior e com maior propensão para
falhas.
Para não teres esses problemas visita as nossas lojas iStore.
Podes consultar a tabela de preços aqui.
Segue estes passos antes de nos trazer o teu dispositivo para ser assistido, para proteger a tua
informação pessoal e poupar tempo:
-Efetua um backup
-Tem pronta a palavra passe do teu Apple ID. A grande maioria das intervenções exige que a
funcionalidade encontrar iPhone seja desativada para prosseguir. Caso te tenhas esquecido da
palavra passe do teu Apple ID, começa por aqui.
-Tem presente ou acessível a prova de compra ou fatura de aquisição do equipamento,
especialmente se o mesmo já tiver sido assistido ou se já tiver passado mais do que um ano desde
a data de compra.
Se preferires podes efetuar uma marcação para assistência. Algumas intervenções podem ser
concluídas em cerca de duas horas, dependendo do problema e do dispositivo a ser assistido.
Podes obter mais informações aqui.
Nota: Se não conseguires desativar a funcionalidade “Encontrar iPhone” pode não ser possível
prestar assistência ao teu dispositivo. Esta política evita que alguém possa prestar
assistência ao teu dispositivo sem o teu conhecimento. Segue os passos aqui caso não te
lembres da sua password.
O nosso diagnóstico tem o valor de 45€ para portáteis e desktops e 25€ para os restantes
dispositivos. Para equipamentos recolhidos em tua casa, o valor do diagnóstico inclui o valor de
transporte.
Coloca o teu dispositivo numa caixa de forma a que fique com pelo menos 2 a 3 cm de espaço entre
o mesmo e as paredes da caixa. Usa material de enchimento suficiente para que o mesmo não se
mexa se a caixa for abanada. Assegura-te que o dispositivo não está nunca em contacto com as
paredes da caixa. O nosso sistema atribuir-te-á um número à altura da criação do processo e o
estafeta levará todo o material necessário para identificar o volume, pelo que não será
necessário que coloques remetente ou destinatário no volume. Entraremos em contacto contigo à
altura da receção do teu dispositivo nas nossas instalações.
Para reparações simples ou upgrades normalmente completamos a reparação em cerca de 3 a 5 dias
úteis depois de nos chegar. Para reparações mais elaboradas, ou com sintomas mais difíceis de
replicar, a reparação pode levar até 10 dias úteis, mas normalmente são completadas em cerca de
7. Todas as reparações que envolvam encomenda de componentes com baterias levam um mínimo de 7
dias úteis em virtude das restrições de circulação das mesmas no espaço aéreo europeu.
Peças
As peças usadas em reparações Apple têm a garantia de um mínimo de 1 ano. Caso a fatura original (ou
da reparação fora de garantia) seja emitida em nome de um consumidor final as peças (e o serviço
associado) têm 2 anos de garantia.
Ativar a garantia
Para poderes utilizar a garantia do teu dispositivo, contacta-nos e o nosso apoio ao cliente terá
todo o gosto em ajudar-te.
Na iStore usamos apenas peças Apple genuínas e componentes originais.
Algumas peças não originais, como carregadores e baterias, poderão ter falhas de conceção que
levem a problemas de segurança.
Existem ainda ecrãs não originais de qualidade bastante inferior e com maior propensão para
falhas.
Para não teres esses problemas visita as nossas lojas iStore.
Podes consultar a tabela de preços aqui.
Segue estes passos antes de nos trazer o teu dispositivo para ser assistido, para proteger a tua
informação pessoal e poupar tempo:
-Efetua um backup
-Tem pronta a palavra passe do teu Apple ID. A grande maioria das intervenções exige que a
funcionalidade encontrar iPhone seja desativada para prosseguir. Caso te tenhas esquecido da
palavra passe do teu Apple ID, começa por aqui.
-Tem presente ou acessível a prova de compra ou fatura de aquisição do equipamento,
especialmente se o mesmo já tiver sido assistido ou se já tiver passado mais do que um ano desde
a data de compra.
Se preferires podes efetuar uma marcação para assistência. Algumas intervenções podem ser
concluídas em cerca de duas horas, dependendo do problema e do dispositivo a ser assistido.
Podes obter mais informações aqui.
Nota: Se não conseguires desativar a funcionalidade “Encontrar iPhone” pode não ser possível
prestar assistência ao teu dispositivo. Esta política evita que alguém possa prestar
assistência ao teu dispositivo sem o teu conhecimento. Segue os passos aqui caso não te
lembres da sua password.
O nosso diagnóstico tem o valor de 45€ para portáteis e desktops e 25€ para os restantes dispositivos. Para equipamentos recolhidos em tua casa, o valor do diagnóstico inclui o valor de transporte.
Coloca o teu dispositivo numa caixa de forma a que fique com pelo menos 2 a 3 cm de espaço entre o mesmo e as paredes da caixa. Usa material de enchimento suficiente para que o mesmo não se mexa se a caixa for abanada. Assegura-te que o dispositivo não está nunca em contacto com as paredes da caixa. O nosso sistema atribuir-te-á um número à altura da criação do processo e o estafeta levará todo o material necessário para identificar o volume, pelo que não será necessário que coloques remetente ou destinatário no volume. Entraremos em contacto contigo à altura da receção do teu dispositivo nas nossas instalações.
Para reparações simples ou upgrades normalmente completamos a reparação em cerca de 3 a 5 dias úteis depois de nos chegar. Para reparações mais elaboradas, ou com sintomas mais difíceis de replicar, a reparação pode levar até 10 dias úteis, mas normalmente são completadas em cerca de 7. Todas as reparações que envolvam encomenda de componentes com baterias levam um mínimo de 7 dias úteis em virtude das restrições de circulação das mesmas no espaço aéreo europeu.
As peças usadas em reparações Apple têm a garantia de um mínimo de 1 ano. Caso a fatura original (ou da reparação fora de garantia) seja emitida em nome de um consumidor final as peças (e o serviço associado) têm 2 anos de garantia.
Ativar a garantia
Para poderes utilizar a garantia do teu dispositivo, contacta-nos e o nosso apoio ao cliente terá todo o gosto em ajudar-te.